WhiteSource
Warning
This page is now hosted on https://odp.finos.org/docs/development-infrastructure/code-validation/whitesource
Responsible Disclosure
WhiteSource is used by FINOS to automate processes around responsible disclosure of security vulnerabilities; read more on /wiki/spaces/FINOS/pages/1230176257
Near Real Time scanning
- At build time, using the WhiteSource unified agent
- On code change, using the WhiteSource integration for GitHub.com
WhiteSource provides a dedicated instance to validate and enforce security and legal compliance for all Symphony Software Foundation hosted projects.
Below are listed the main WhiteSource features that have been adopted by Foundation projects.
- Check libraries for outdated versions
- Check libraries for security vulnerabilities
- Check libraries for bugs
- Check libraries for problematic/undefined licenses
- Check libraries for release activity
- Integration with CI environments
This page gives an introduction to the WhiteSource Dashboard, see below how to request access; to enable automated scanning, project leads can use the WhiteSource Unified Agent in their build process and configure different type of actions.
Glossary
To avoid confusion, below are listed some WhiteSource concepts that differ with the definitions used within the Foundation.
- A Foundation repository is a Github repository hosted by the Foundation; in WhiteSource terms, this is called a project
- A Foundation project is a logical entity that includes
- one or more project leaders
- a project team
- one or more Foundation repositories; if one, project and repository will have the same name.
- In WhiteSource terms, this is called a product and can be accessed directly by the WhiteSource main menu; each WhiteSource product will list below the projects included.
- Foundation WhiteSoure dashboard - WhiteSource provides a dedicated instance for the Foundation projects that can be accessed
- by all project leaders, to check and export project metrics
- by Foundation Staff, to configure Foundation WhiteSource policies
- Foundation WhiteSource policies - A collection of rules and workflows implemented in the WhiteSource dashboard by the Foundation team to enforce security and legal compliance; below are reported the details.
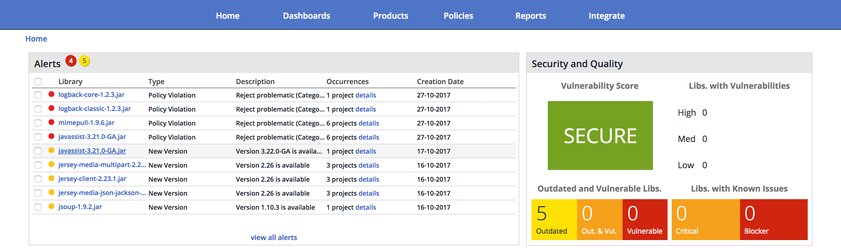
- Alert - The visual notification that WhiteSource shows in the main dashboard when a policy violation is found
Features
WhiteSource provides the following features to Foundation project leads/committers that have been granted access:
- Access the WhiteSource dashboard for one or more projects
- Access WhiteSource Due Diligence and Risk reports
- Browse (and drill down) through project libraries
- Browse (and drill down) through licenses found in the project
- Check alerts and warnings triggered by policy violations
- Configure WhiteSource build plugins to upload project metrics
- Configure Travis CI (or other CI environments) to continuously
- validate code against Foundation policies enforced by WhiteSource
- fail the build, if any policy violation is found
- upload project metrics to the WhiteSource Foundation dashboard
WhiteSource Policies
Legal policies disabled
Legal policies are currently disabled due to the large amount of false positive generated by dual-licensed libraries. We are working to improve such configuration
Below are the WhiteSource policies that have been configured by the Foundation and are enforced across all integrated projects; all libraries that are scanned in a project are matched against the following policies, in the order reported below, until a policy is matched.
- [SECURITY] Reject High Security Vulnerability Severity - any library that contains high level CVEs is marked as Rejected,
- [SECURITY] Reject High Security Vulnerability Score - any library that contains CVEs with score higher than 7 is marked as Rejected,
- [QUALITY] Reject High Bug Rating - any library high bug rating is marked as Rejected,
- [LEGAL] Licenses that require review - any library with unknown license is marked as Rejected,
- [QUALITY] Reassign Low Version Activity - any library with a low amount of versions released is Reassigned to the project lead for validation,
- [QUALITY] Reassign Stale (5 years) Library - any library without a release for more than 5 years is Reassigned to the project lead for validation,
- [LEGAL] Reject Problematic (Category X license) libraries - any library using a Category X license, as indicated in our /wiki/spaces/FINOS/pages/75530255/wiki/spaces/FINOS/pages/75530375/wiki/spaces/FINOS/pages/75530255, are marked as Rejected.
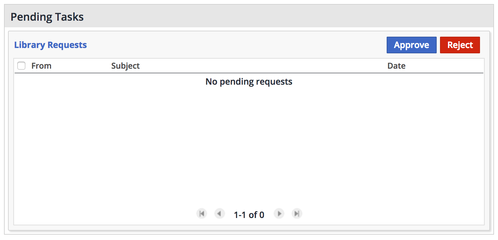
Managing requests
Every time a policy reassigns an alert (see policies above), a user gets notified with an email by WhiteSource that something needs attention; using the Dashboards > Requests it is possible to check the Pending requests.
Generating reports
WhiteSource generate a wide list of Reports and Dashboards, that can be accessed by the main menu; below are listed the ones that have been used most frequently by Foundation projects.
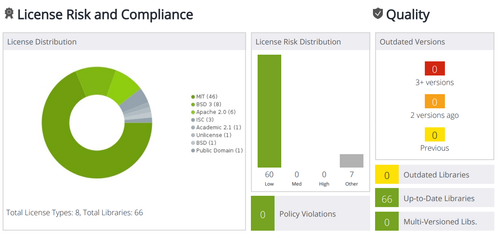
Reports > Risk, generates a summary a management level 1-Pager, providing a bird's-eye view of all aspects concerning the account's open source libraries; security, quality and compliance. It can be exported to PDF and attached to the project's documentation, to give consumers peace of mind.
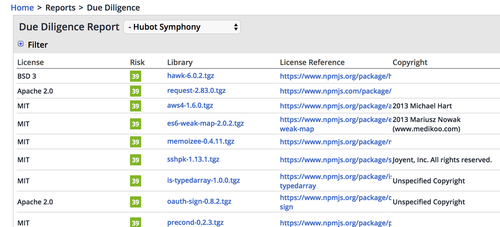
Reports > Due Diligence, a list of all libraries and licenses, allowing to filter, drill down and spot unwanted items; it is a useful tool to perform thorough checks and validate that policies have been correctly appied.
Reports > Ignored alerts, the list of alerts that have been ignored and the comments; this list must be periodically checked/updated by project leads and preferably kept empty.
Reports > Effective Licenses, the list of licenses that have been manually defined; this list must be periodically checked/updated by project leads and preferably kept empty.
Request access
In order to access the WhiteSource dashboard, you first need to be invited by Foundation Staff; open a HELP issue or send an email to help@finos.org, with the title Request access to WhiteSource and in the description specify:
- the email address you'd like to use to login
- the Foundation project you would like to scan with WhiteSource
If you login for the first time in WhiteSource and no project have been registered yet, the dashboard will look empty; check how to configure your build in order to upload your first project metrics.
Related content
Need help? Email help@finos.org we'll get back to you.
Content on this page is licensed under the CC BY 4.0 license.
Code on this page is licensed under the Apache 2.0 license.