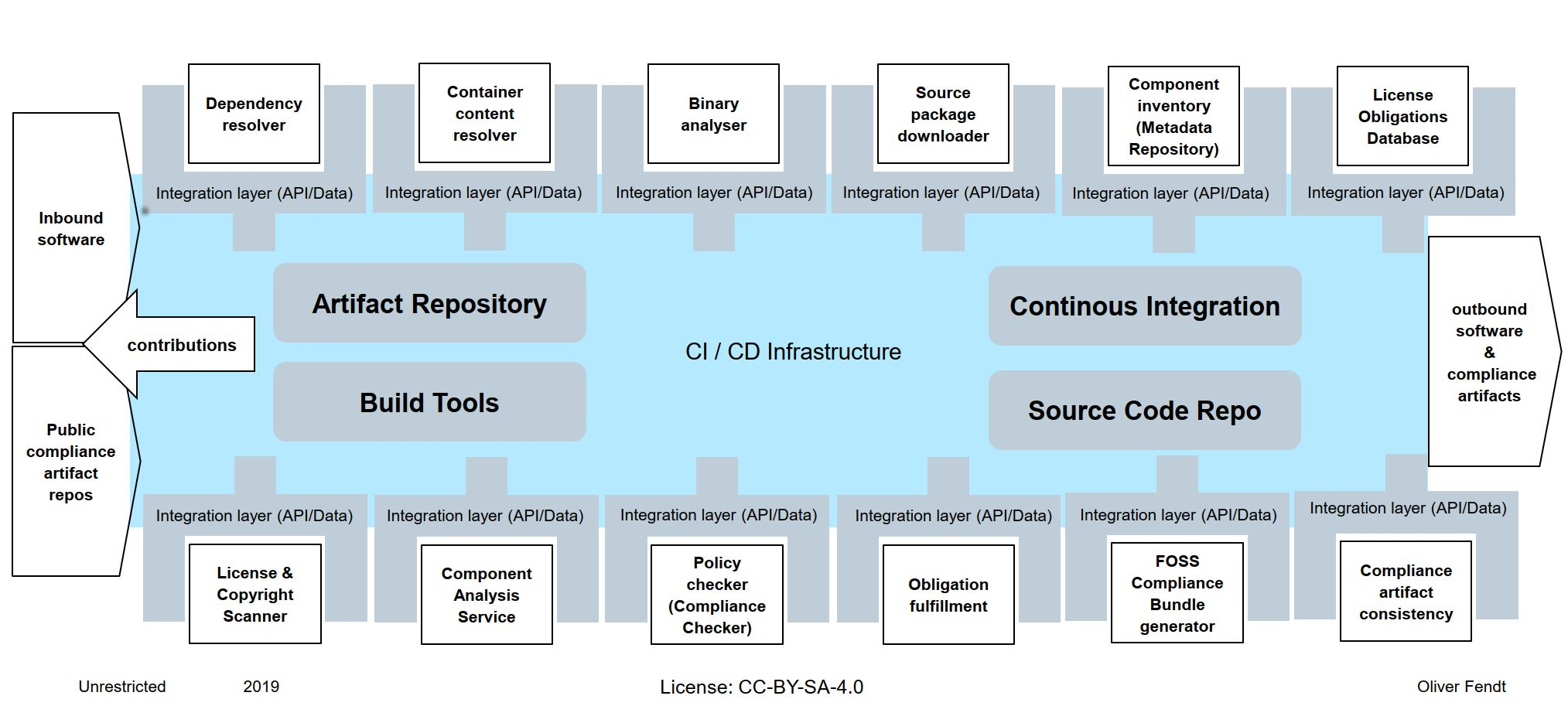
Open Source Compliance Workflows
Below are some high-level workflows for common open source compliance processes. To provide a point of reference for the various steps, the workflows refer to the functional components of an open source compliance toolchain in the diagram below, produced by the Open Source Tooling group of the OpenChain Project.
Continuous compliance via CI/CD (DRAFT)
- Developer makes commit to product Source Code Repo
- Catalog open source dependencies
- Identify open source dependencies
- Continuous Integration initiates automated build via Build Tools, producing product build artifacts
- Package dependencies
- Dependency Resolver integrates with Build Tools to generate a list of package dependencies to be retrieved from Artifact Repository (including first-order and transitive, i.e. dependencies of dependencies)
- Component Inventory for product is updated to include metadata about all dependencies identified
- Source dependencies
- License & Copyright Scanner is run on product Source Code Repo and generates list of files with apparent open source license or copyright statements
- Component Analysis Service is run on product Source Code Repo and generates list of open source components whose code is used within
- Component Inventory for product is updated to include metadata about all dependencies identified
- Container dependencies
- Container Content Resolver is run on any container images among product build artifacts to generate bill of materials for packages within
- Component Inventory for product is updated to include metadata about all dependencies identified
- Binary dependencies
- Binary Analyser is run to inspect any binary artifacts among product build artifacts and scan for open source artifacts within (potentially in conjunction with License & Copyright Scanner, Component Analysis Service and Container Content Resolver) and generates 1) list of open source components identified and 2) list of files with apparent open source license or copyright statements
- Component Inventory for product is updated to include metadata about all dependencies identified
- Check dependencies against policies
- Run Policy Checker to determine whether open source dependencies include any unapproved packages or licenses
- Fail build if Policy Checker finds violations
- (Asynchronous) Human review of source code and build artifact dependencies
- Personnel (e.g. Open Source Review Board) review output of License & Copyright Scanner and Component Analysis Service to determine whether there are any open source dependencies in Source Code Repo or among product build artifacts that were not automatically identified
- Newly identified open source dependencies are added manually to Component Inventory (with special attention to any modifications)
- Identify open source dependencies
- Produce compliance materials
- Collect source code for open source dependencies
- Run Source Code Downloader to add source code for any new dependencies to Artifact Repository
- For open source dependencies used in modified source code form, add modified source code to Artifact Repository
- FOSS Compliance Bundle Generator:
- Retrieves license obligations for each open source component from License Obligation Database
- Runs Obligation Fulfillment to produce: 1) where possible, compliance artifacts for open source dependencies (i.e. of license text, legal attribution statements, and source code where required) and 2) audit trail flagging any issues or components requiring further review
- Compliance Artifact Consistency is run on compliance artifacts to identify any issues
- Personnel (e.g. Open Source Review Board) review audit trail and compliance materials and amend or supplement as needed
- Collect source code for open source dependencies
Product release
External open source contribution
Open source project release
New open source dependency
Need help? Email help@finos.org we'll get back to you.
Content on this page is licensed under the CC BY 4.0 license.
Code on this page is licensed under the Apache 2.0 license.